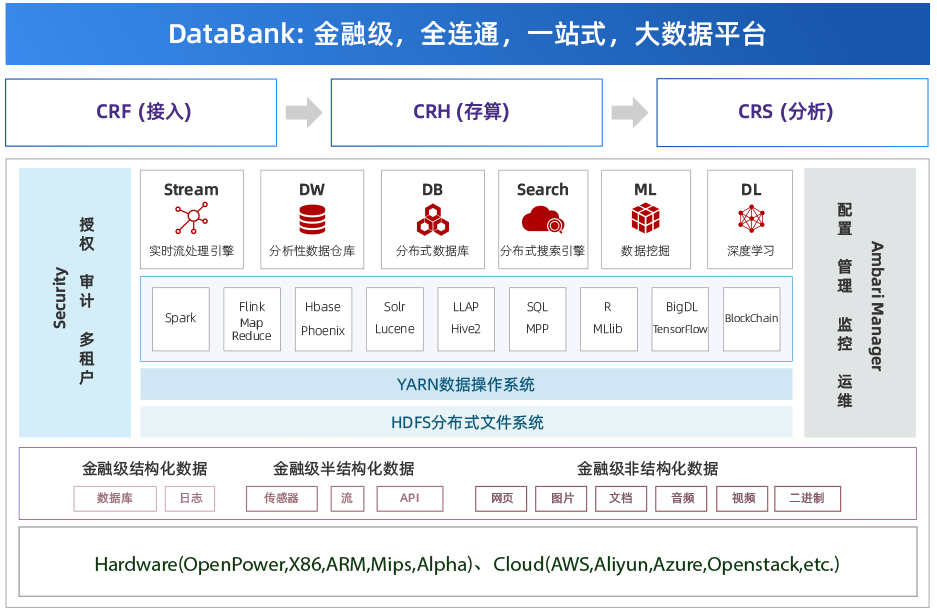
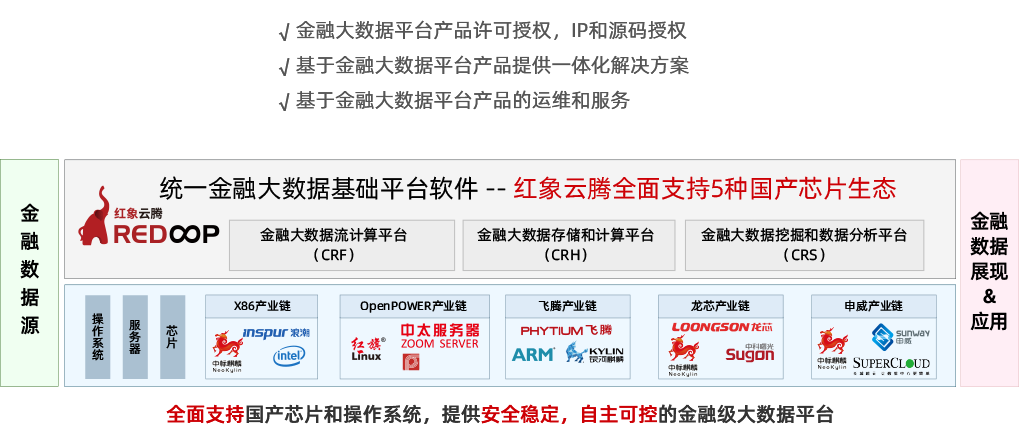
J9老哥俱乐部 Enterprise(代号“CRH”)是大数据基础软件。支持 Hive、Spark、Kafka、Flink、Doris、Hudi 等开源大数据生态软件,支持界面化安装、配置、监控各种大数据软件,以Apache Ambari为管理平台,基于 Apache Hadoop、Apache Hbase 为存储和计算核心。 提高交付效率,降低软件故障,降低学习和维护成本,整体提升企业大数据运行效率。
立即安装
一键安装分布式软件,通过界面化安装Apache Hadoop大数据生态30+多个软件。

支持界面化修改启动脚本和后台参数配置。

支持对组件状态,关键指标的监控,全面了解集群现状。

支持通过组件地址配置,重启后即可实现快速升级

支持Hadoop生态集群组件HA高可用,包括 HDFS,YARN,HBASE高可用

通过Kerberos+Ranger+OpenLDAP支持集群访问安全和数据访问安全。
 产品快速迭代,快速体验新特性
产品快速迭代,快速体验新特性
 开放 & 开源生态,上下游社区项目丰富
开放 & 开源生态,上下游社区项目丰富
 广泛的社区用户 & 开发者支持
广泛的社区用户 & 开发者支持
 提供商业产品技术支持服务
提供商业产品技术支持服务
 专业商业支持团队(电话、IM、邮件、现场)
专业商业支持团队(电话、IM、邮件、现场)
 产品故障支持最高响应级别 7*24
产品故障支持最高响应级别 7*24
 商业专家支持服务(规划/实施/主动式巡检/故障协查/知识转移/重要时期保障)
商业专家支持服务(规划/实施/主动式巡检/故障协查/知识转移/重要时期保障)
 快速部署,轻松进行集群部署和管理
快速部署,轻松进行集群部署和管理
 支持aws s3 等对象存储
支持aws s3 等对象存储
 商业专家支持服务
商业专家支持服务
 支持统一权限安全增强
支持统一权限安全增强
| 界面安装 | 参数配置 | 指标监控 | |
|---|---|---|---|
| 管理组件 | |||
| Ambari 集群管理 |  |
 |
 |
| 核心组件 | |||
| HDFS分布式存储引擎 |  |
 |
 |
| YARN分布式调度引擎 |  |
 |
 |
| HBASE 引擎 |  |
 |
 |
| 计算引擎 | |||
| Hive 引擎 |  |
 |
 |
| Spark 引擎 |  |
 |
 |
| Flink 流计算引擎 |  |
 |
 |
| 企业安全增强 | |||
| Kerberos 访问控制支持 |  |
 |
 |
| Ranger 权限控制支持 |  |
 |
 |

云和恩墨以“数据驱动、成就未来”为使命,构建数据驱动的智能未来,致力于将数据技术带给每个行业、每个组织。我们在基础软件、数据和云软件、数据服务等领域为企业提供可信赖的产品、J9老哥俱乐部 和服务,为成就未来敏捷高效的数字世界而不懈努力。

汇丰银行

昆仑保险经济

大港油田

烟台惠通

紫光华山

西安交通大学

五舟科技

麦思博软件

科达数码

北明软件

网润恒信

联想

阳光耐特

烽火通信

利为软件

中太服务器

辽宁交通厅

荣之联

云途腾

安荣科技

易观智库

瑞德云

银河麒麟

青藏铁路

博纳通

中科软科技

国通科技

中国资源卫星应用中心

中国运载火箭技术研究院

北京汽车

中科天玑

玛达科技

国家体育总局

中北大学

中国人民解放军大学